Tools to Meet Compliance Benchmarks
Kandji’s built-in library of security settings takes the guesswork out of guarding your devices.

Why use Kandji for compliance
Map to CIS and NIST benchmarks with a click, building a formidable foundation for security. Reach compliance with SOC 2, FedRAMP, HIPAA, or ISO27001 at record speed with Kandji’s security setting library.
Security controls templatized to industry benchmarks
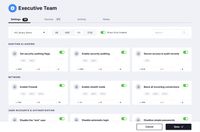
Security controls organized into templates for CIS Level 1 and CIS Level 2 allow you to reach compliance with benchmarks at the click of a button.
Continuous enforcement
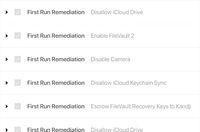
Kandji continuously enforces everything from endpoint protection to encryption to password policies on all devices—even when devices are offline.
Auditor access
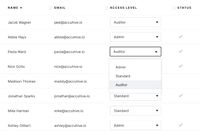
Prove compliance and provide detailed reporting at a moment’s notice using “read-only” auditor access mode.
Automated evidence collection
Integrate with third-party providers to continuously monitor and collect evidence from your endpoints into the systems that prove infrastructure compliance.

See Kandji in action
Assign dozens of security settings and ensure your fleet meets CIS benchmarks—in minutes.
Continuously enforce endpoint protection across your fleet. Kandji provides ready-to-execute audit and enforce scripts.
Encrypt all data on Mac computers with the recovery keys escrowed in Kandji and rotated frequently.
Easy Reporting
Generate comprehensive Apple fleet reports on key categories, with a few clicks and a simple interface.


Manage and secure your Apple devices at scale.
