Managing Network Settings on macOS Big Sur and MAC Address Randomization in iOS 14
 Kandji Team
Kandji Team
A lot of exciting changes have come to macOS Big Sur and iOS 14. In this guide, we’re going to do a deep dive into managing network settings in Big Sur, and then we’ll break down the new MAC address randomization feature in iOS 14. Here’s a quick overview of what we’ll cover:
networksetup: Changes in macOS Big Sur- What’s the new MAC Address Randomization Feature?
- Implications for IT: MAC Address Randomization and MDM
networksetup: Changes in macOS Big Sur
The networksetup utility is a command-line interface that IT can use to configure network settings within Terminal. Apple introduced a few new features to the networksetup tool in macOS Big Sur, and they’ve revamped which types of users can use its advanced capabilities. In this section, we’ll provide an overview of the current capabilities of the networksetup tool, and then we’ll discuss the new limitations placed on standard users.
What Can networksetup Do?
We’ll list a few of the capabilities the networksetup tool can accomplish below. For more information about command-line syntax, see Apple’s networksetup documentation or use the help prompt by entering networksetup – help.
List Network Services: Entering the command [-listallnetworkservices] will display all network services on the computer’s hardware ports. If an item is marked with an asterisk, it’s currently disabled.
Set to Manual: You can set the TCP/IP configuration for the specified network service to manual. Simply enter -setmanual, specify the network service, set IP address to ip, Subnet Mask to subnet, and Router address to router.
networksetup -setmanual networkservice ip subnet router
Set to DHCP: Dynamic Host Configuration Protocol (DHCP) dynamically assigns IP addresses to each device on the network. You can set the TCP/IP configuration for the specified network service to use DHCP. To do this, enter -setdhcp and specify the network service. Optionally, you can specify a client id or leave this section empty to clear the DHCP client id.
networksetup -setdhcp networkservice [clientid]
Set to BOOTP: Bootstrap Protocol (BOOTP) is a static protocol that supports manual configuration of IP addresses. You can set the TCP/IP configuration for the specified network service to use BOOTP by entering -setbootp and specify the network service.
networksetup -setbootp networkservice
Specify Manual IP for DHCP: You can specify the manual IP address to be used for DHCP for a network service:
networksetup -setmanualwithdhcprouter networkservice ip
Specify DNS Servers: You can specify the IP addresses of servers you want a certain network service to use to resolve domain names. To clear all DNS entries for that network service, type empty in place of DNS server names.
networksetup -setdnsservers “Ethernet” 192.168.100.100 192.168.100.12
Designate Search Domain: You can designate the search domain for the specified network service. To clear all search domain entries for that network service, type empty in place of the domain name.
networksetup -setsearchdomains “Ethernet” example.com foo.com
Set Web Proxy: You can set Web proxy for a network service with domain and port numbers. Specify off to disable authenticated proxy support. Specify on to enable authenticated proxy support, and then enter your user name and password.
networksetup -setwebproxy “Ethernet” proxy.company.com 80 on steve mypassword
Limitations for Standard Users
The networksetup tool is accessible to any user on a Mac and can be easily accessed through Terminal. Previously, standard users and administrators had the same capabilities. This meant that anyone could achieve the capabilities listed in the last section and view and edit network settings from the command line.
To improve security in macOS Big Sur, Apple placed limitations on standard users who access networksetup. Now, each account type has its own abilities. As a rule of thumb, if changing the setting in the System Preferences page requires unlocking a padlock, the equivalent setting in the networksetup tool will require a password.
Administrators still have complete control over the tool. However, standard users will need administrator authorization to do anything beyond reading network settings, turning Wi-Fi power on or off, or changing the Wi-Fi access point.
Other Networking Changes in Big Sur
There are a few other networking changes released in macOS Big Sur as well. We’ll take a look at a few of them here:
- Network Utility app is deprecated: The long-standing Network Utility app is being deprecated. This tool displayed information and troubleshooting tools that let users check their network connection. The functionality can be replicated by using Terminal commands, and the Wi-Fi functions can be replicated by the Wireless Diagnostic app.
- Safari gets a new privacy reporting tool: Safari is getting even more privacy features. In macOS Big Sur, users can see which tracking cookies a site is using and which ones Safari has blocked. Safari 14 also has HTTP/3 enabled by default.
- Chrome and Firefox extensions coming to Safari: With macOS Big Sur and Xcode 12, developers can port existing Chrome and Firefox extensions to be used with Safari 14 using
xcrun safari-web-extension-converter. Along with this change, Apple is introducing new user controls for managing browser extensions. To manage the risk of malicious extensions entering Safari 14, Apple insists that browser extensions only be distributed through the App Store.
MAC Address Randomization: What IT Needs to Know
As of iOS 14, devices use randomized Media Access Control (MAC) addresses when associating with Wi-Fi networks. This new feature is called private address, and it will be enabled by default on all iOS 14, iPadOS 14, and watchOS 7 devices. Users can manage this setting at any time in device settings–unless their device is enrolled in MDM and the setting is turned off via a Wi-Fi profile for a specific network. Using Kandji as your MDM solution, you can disable this feature within the Wi-Fi profile.
In this section, we’ll explore the capabilities of this new MAC address randomization feature in more depth. We’ll also briefly discuss another feature that gives users more control over their privacy: local network access control. This feature triggers a prompt requesting user approval whenever an app tries to access a local network.
How Does MAC Address Randomization Work?
Apps can gather information about users from the local networks they use. This can include information such as the user’s location and their proximity to other users. Apps can also build a profile of the user based on other connected devices, such as Apple TVs or other accessories.
MAC addresses are identifiers used to address specific devices on a network. While MAC addresses aren’t supposed to be used to track devices, apps used to be able to use them for this purpose. That’s why Apple introduced MAC address randomization in iOS 8, which made sure users couldn’t be tracked by their MAC address when they weren’t connected to Wi-Fi. In this case, only the MAC address that the device broadcasted during probing (while not connected to a network) would be randomized.
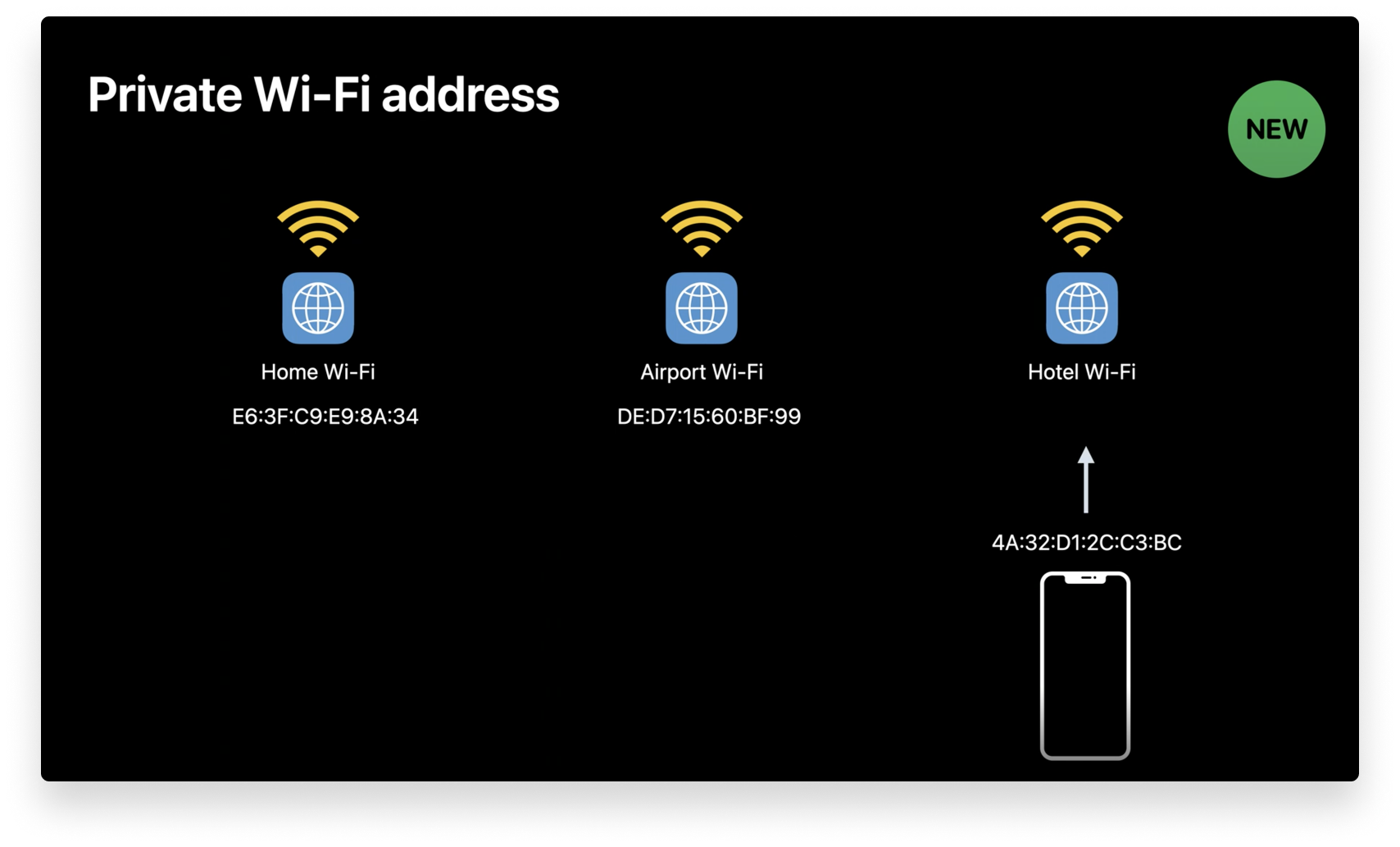
Image source: developer.apple.com
However, once the user is connected to a Wi-Fi network, their physical MAC address still leaves a trace. Whenever a device connects to a Wi-Fi network, it identifies itself with this static private Wi-Fi address. For instance, if employees connect to Wi-Fi at the office, the airport, and then a hotel, network operators can use the MAC address “breadcrumb trail” to sketch a more complete picture of where the users have been and what network activity they engaged in. This will no longer be possible on iOS 14.
At WWDC 2020, Apple announced that iOS 14, iPadOS 14, and watchOS 7 will use a new feature called private Wi-Fi address. This feature automatically manages Wi-Fi MAC addresses when users join networks, generating per-network addresses that cannot be linked to their identities. This means users can no longer be tracked from one Wi-Fi network to the next, and that their network activity cannot be tied to them because a unique MAC address is generated for each network. If a device fails to join the network, it will revert back to its hardware MAC address.
Implications for IT: MAC Address Randomization and MDM
As we mentioned earlier, users can manage the private address option at any time in device settings–unless their device is enrolled in MDM and the setting is turned off via network profile. The new private address feature can be accessed by users in Settings > Wi-Fi and then clicking the Information icon next to a network. Here, a private address option will appear.
This feature will be turned on by default in iOS 14, iPadOS 14, and watchOS 7. Using the new private address feature will not change how users join most Wi-Fi networks–they can simply connect to Wi-Fi networks as they normally would. If a user erases all content and settings from their device or uses the Reset Network Settings feature, a new private Wi-Fi address will be generated the next time it connects to the Wi-Fi network.
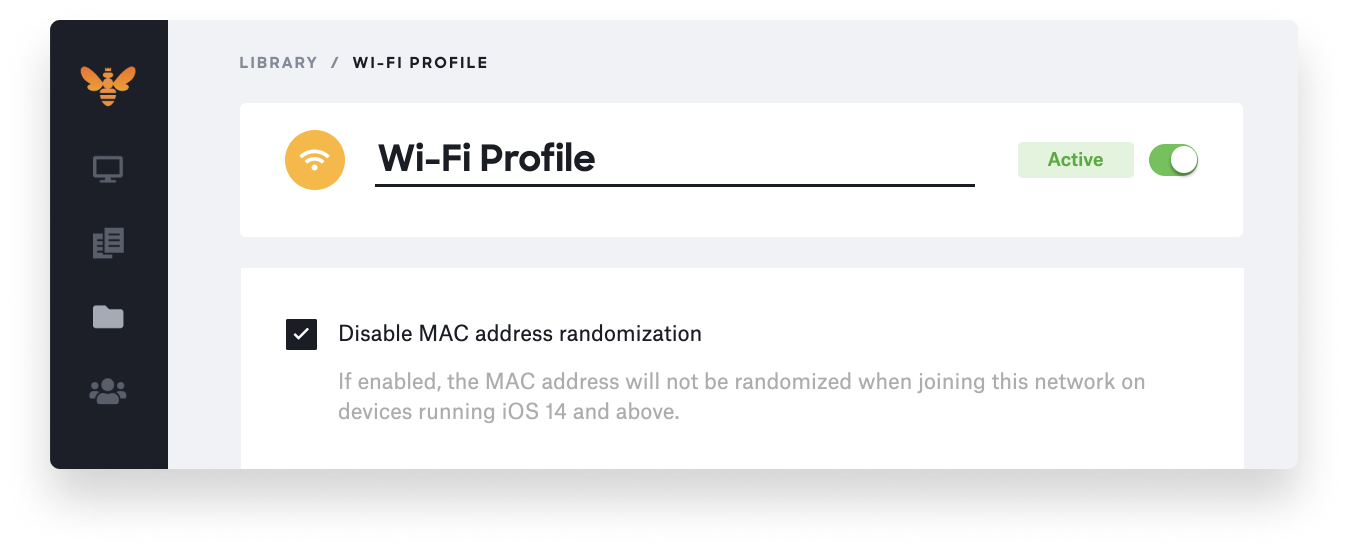
Your organization may need to update its Wi-Fi network security to work with the new private address feature. Otherwise, Apple states in its private address documentation that you can turn it off for your Wi-Fi network by using an MDM-defined network profile. If you’re using Kandji as your MDM solution, this setting can now be disabled with a new option within the Wi-Fi profile.
Joining Previously-Known Networks with a Private Address
When a company device with private address enabled tries to connect to a previously-known network (that is, a Wi-Fi network that the device remembers prior to upgrading to iOS 14, iPadOS 14, or watchOS 7), it will attempt to connect using the private address.
If this attempt fails (for instance, if your organization’s network doesn’t allow devices using a private address to join), the device will immediately connect using its hardware MAC address. Once the connection is successful, the device will turn off the private address option for that network. However, it will still attempt to connect using a private address, and if it’s ever successful, it will only use that private address for future connections.
Joining New Networks with a Private Address
In most cases, devices with private address enabled will use a private address to join new Wi-Fi networks. However, if the device has an MDM profile that turns off the private address setting, it will use the hardware MAC address to join the network. If the device connects to a Wi-Fi network during Setup Assistant, it will use the hardware MAC address to join, and then it will treat the network as a previously known network.
The entire Kandji team is excited to continue building out support for Apple’s latest developments. With innovation and iteration at the core of everything we do, we’re constantly building solutions to give you more of what you need and improve upon features you already love. With Kandji, you can be confident that your Apple fleet is in safe and secure hands from deployment to retirement.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.



