macOS Big Sur and MDM: The Comprehensive Guide for Mac Admins
 Kandji Team
Kandji Team
When macOS Big Sur was first unveiled at the Worldwide Developers Conference (WWDC) 2020, it was clear that Apple was bringing significant changes to the Mac. Beyond completely overhauling user-facing features and design, they’re also making a lot of changes with Mac management in mind.
In this article, we’re going to take stock of the biggest MDM-Big Sur changes, talk a bit about their implications for macOS device management, and share some tips to make your transition to Big Sur smooth.
Update 11/12/20: We're proud to announce release day support in Kandji's device management (MDM) solution for the new features in macOS Big Sur.
We’re going to cover a lot of ground here, so here’s an overview of what you’ll find in this article:
- How to Manage Public Betas and Defer Software Updates
- Changes to macOS Supervision
- Auto Advance has Come to Mac
- Account Creation with SCIM vs. JIT
- Big Changes Come to PPPC
- Changes to Bootstrap Token
- Changes to Kernel Extensions (KEXTs)
- Mac Transitions to Apple Silicon
- Automated Device Enrollment on Big Sur
- Lights Out Management Comes to the Mac Pro
- Managed Apps on macOS Big Sur
- New Content Caching MDM Command
- Security Updates for macOS Big Sur
Managing Public Betas
There are a lot of exciting changes in macOS Big Sur, but transitioning managed devices to the new operating system is going to be a handful for IT administrators. In beta season, it’s a good idea to be running software and service tests to make sure this transition is as smooth as possible.
That’s why we wrote a comprehensive guide to managing public betas on macOS Big Sur. We cover everything you need to know about device management & Big Sur, including:
- Accessing public betas via the Apple Beta Software Program: The Apple Beta Software Program lets IT administrators prepare their environments for new updates by giving them access to pre-release programs.
- Preventing non-testing devices from installing beta software: Because public betas aren’t in their final form, it’s too risky to install them on production devices. We show you how to keep non-testing devices (macOS and iOS) from getting the betas, so your employees can work without interruption.
- Removing public betas from your macOS device: We’ll also walk you through removing a public beta from iOS or macOS devices by either deleting the beta profile or restoring the device to a commercial OS backup.
- Deferring software updates via your MDM solution: Finally, we discuss the software update changes announced at WWDC 2020, including the removal of the software update catalog and the addition of new MDM commands to accept, reject, or defer major OS updates.
We've gotten a lot of questions on how best to manage the deferral and upgrade process, so we surveyed a handful of Mac admins in the community to learn how they are managing the process of deferring software updates and upgrading to Big Sur. To get their advice, read our article 7 Mac Admins Share Perspectives on Deferring and Upgrading to macOS Big Sur.
Changes to macOS Supervision
Supervision gives IT administrators more control over devices, especially when it comes to using MDM to accomplish tasks such as retrieving activation lock bypass codes, retrieving bootstrap tokens, deleting users, and more.
In macOS Catalina, supervision came to the Mac – but it wasn’t nearly as robust out as device supervision on iOS, iPadOS, and tvOS. Supervision on the Mac is really just a change in wording, making anything that once required “DEP enrollment” require “supervision.”
Initially, macOS devices could only be supervised if they were enrolled via Automated Device Enrollment. Because this was the only route to supervision, Automated Device Enrollment and supervision were synonymous – the capabilities available to supervised devices were exclusive to this enrollment method.
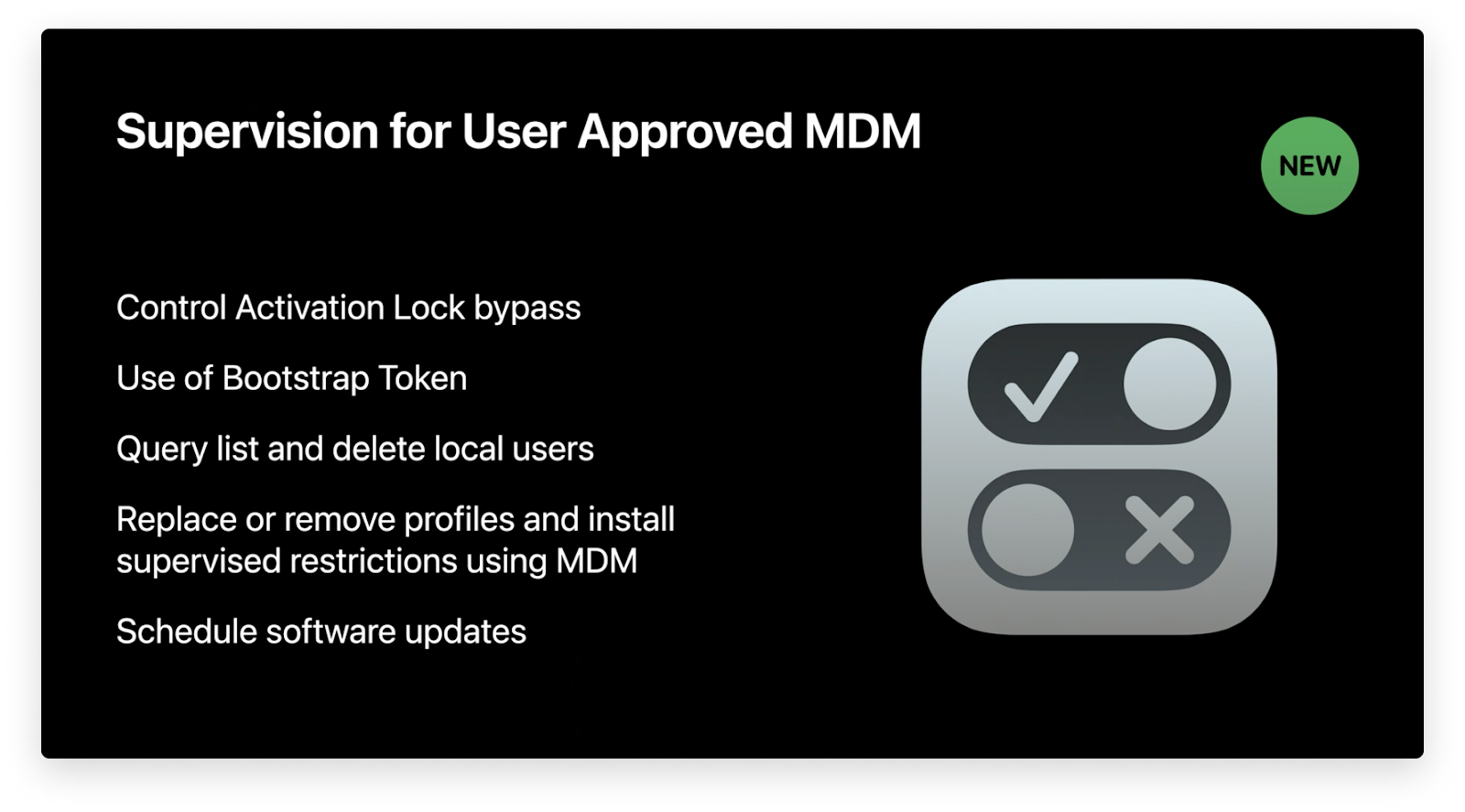 Image source: developer.apple.com
Image source: developer.apple.com
In macOS Big Sur, that changes. At WWDC 2020, Apple announced that macOS devices enrolled via manual Device Enrollment with a User-Approved MDM status will also be considered supervised. There is a small caveat to this method of achieving device supervision, which is discussed in the Kernel Extension portion of this guide.
Read More About Supervision and MDM (Big Sur):
Although manual Device Enrollment can now lead to device supervision, there are still a couple of reasons why Automated Device Enrollment is still the best approach. You can read about this at length in our guide to changes in macOS supervision.
Auto Advance has Come to Mac
Auto Advance is an enrollment feature that makes it faster to set up devices at scale. The Auto Advance capability was initially introduced to streamline Apple TV device deployment. IT simply had to enable Auto Advance on any Apple TV that leveraged Automated Device Enrollment.

Image source: developer.apple.com
This makes it much easier for IT or users to set up Apple TVs. Rather than manually proceeding through Setup Assistant for every new device, Auto-Advance enabled devices can automatically bypass Setup Assistant so employees can use the device faster. The feature also lets you achieve unique workflows like automatically locking an Apple TV in presentation mode.
In macOS Big Sur, Auto Advance is coming to Mac. Similar to its Apple TV counterpart, when Auto Advance is enabled for a Mac, IT and users can completely bypass Setup Assistant. All that’s required is a power cord, an ethernet cord, and then turning the Mac on. The user will land on the login window faster, and the device will automatically be managed according to your business’ needs.
In lab environments or any other application where a large number of Mac computers are used, this is a game-changing update. Rather than manually setting Mac computers up one-by-one, Auto Advance for Mac will let users land on the login screen or go through a customized setup process defined by IT.
Read More About Auto Advance and MDM (Big Sur):
You can read more about this in our guide to Auto Advance for Mac. In that guide, we’ll walk you through the history of Auto Advance, and we have a step-by-step guide to using Auto Advance for tvOS or macOS.
Account Creation with SCIM
Although not exclusive to macOS Big Sur, Apple recently introduced a new method to to create Managed Apple IDs and streamline the employee login experience. If your business leverages Azure Active Directory as an identity provider (IdP), then you can use Federated Authentication to link your IdP with Apple Business Manager. What makes this possible is Apple’s implementation of SCIM (System for Cross-domain Identity Management).
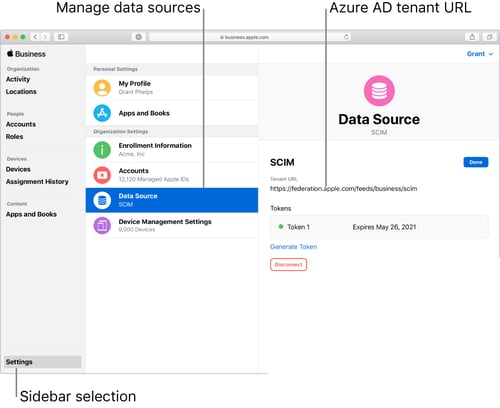
Image source: support.apple.com
In a nutshell, SCIM lets IT automatically provision and deprovision users from Active Directory in Apple Business Manager. This wasn’t possible using the previous just-in-time (JIT) account creation method, which simply created accounts when a user signed into a Managed Apple ID with their Azure Active Directory credentials.
With JIT, if an Active Directory account is deactivated, it couldn’t be automatically deprovisioned in Apple Business Manager. SCIM, on the other hand, automatically creates new accounts as new people join your IdP, and it automatically deletes those accounts as users are removed from the IdP.
Read More About SCIM and Device Management (Big Sur):
For a deep dive into this topic, you can read our guide to Managed Apple ID creation with Azure AD using SCIM & JIT, which is packed with everything you need to know about account creation with SCIM, including a step-by-step guide to set up and configure it.
Big Changes Come to PPPC
Back in macOS Mojave, Apple debuted a set of security controls called Privacy Preferences Policy Control (PPPC), which gave IT more control over cross-application data requests. PPPC essentially let IT decide if certain apps could access protected user and system resources without user approval.
In macOS Catalina, standard users had the ability by default to approve apps to access sensitive system features (like Contacts, Screen Capture, and microphone). However, IT had no power to enable these features via MDM – they were all considered “deny only.”
That changed in an early beta of macOS Big Sur. This update to PPPC prevented standard users from approving applications for sensitive system-level PPPC controls, such as Screen Capture and Input Monitoring. However, this made it impossible for standard users to approve access requests for common business apps, like Zoom.
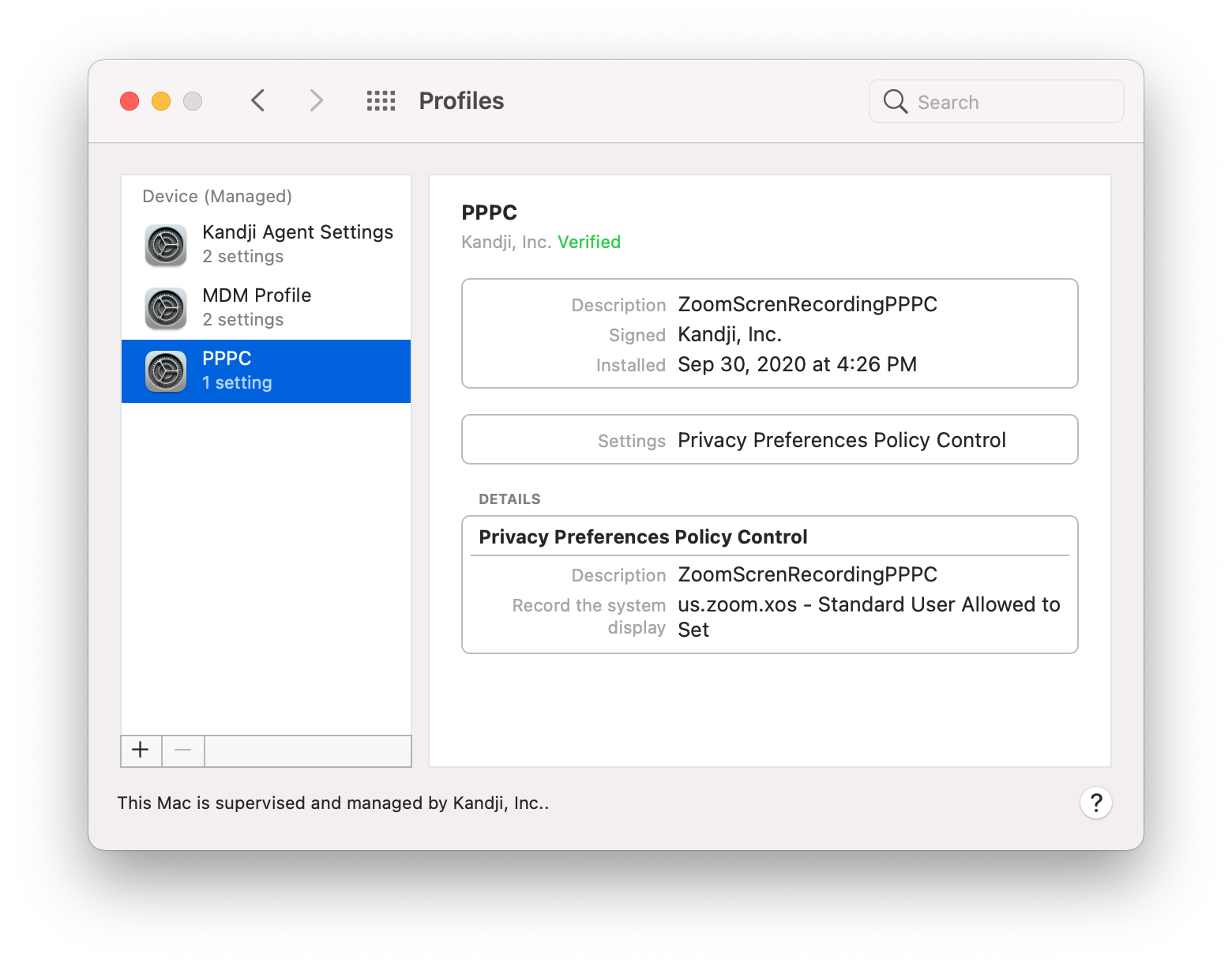
That’s where the most recent PPPC update comes in. Now, IT can use an MDM solution and the PPPC profile to allow standard users to approve defined applications for Screen Capture and Input Monitoring. In other words, IT can create a list of apps that allow standard user approval.
Read More About PPPC, MDM, & Big Sur:
For a deep dive into the latest PPPC update, you can read our guide to PPPC changes in macOS Big Sur. We’ll walk you through the setup process for defining which apps allow standard user approval.
Changes to Bootstrap Token
At WWDC 2020, Apple announced that Bootstrap Tokens are now required to approve and load Kernel Extensions (KEXTs) via MDM on future Apple Silicon devices running macOS Big Sur. This means IT won’t be able to complete tasks like installing updates via MDM without a Bootstrap Token on these future devices.
Now with Bootstrap Tokens on macOS Big Sur, IT no longer has to create complicated workflows to grant SecureToken attributes to macOS accounts. Before macOS Big Sur, Bootstrap Tokens could only be used to grant SecureToken to network accounts and Auto Admin accounts created via MDM. Now, Bootstrap Tokens can automatically grant SecureToken to any local account when it signs into the Mac computer.
Bootstrap Tokens were introduced in macOS Catalina as encryption keys provided to an MDM server. They previously only assisted with enabling SecureToken for mobile network accounts or the Auto Admin account. Now with macOS Big Sur, Bootstrap Tokens will be leveraged to grant every user SecureToken when they sign in (this applies only if they sign in graphically), not just network accounts or the Auto Admin.
Secure Token will be granted to the first account whose password is set. This excludes an Auto Admin account as the password for that account is set using a hash via MDM, and when creating a Secure Token, macOS requires the password to be available in plain text. Auto Admins can still be granted secure token simply by signing into the account graphically.
Another important reminder of a change made in macOS Catalina 10.15.4 is that macOS will automatically attempt to generate and escrow a Bootstrap Token to MDM anytime a Secure Token enabled user signs in.
Read More About Bootstrap Token, MDM, & Big Sur:
You can read more about this in our guide to Bootstrap Token and SecureToken on macOS Big Sur. In that guide, we also cover the particulars of setting up Bootstrap Token for your MDM and manually generating and escrowing Bootstrap Token via Terminal.
Changes to Kernel Extensions (KEXTs)
At WWDC 2020, Apple announced that when loading Kernel Extensions on macOS Big Sur, a restart that rebuilds the Kernel Cache would need to be initiated by a local administrator via the Security and Privacy System Preferences pane or by MDM via a new option on the restart command.
This could potentially cause workflow issues for organizations installing Kernel Extensions, and want users to be able to initiate the Kernel Cache rebuilding restart outside of a restart being forced via an MDM solution. For organizations that primarily use standard user accounts, these users would not be able to approve a restart that rebuilds the Kernel Cache.
However, in a recent macOS Big Sur beta release, Apple has resolved this by adding a new option for MDM developers in the Kernel Extension payload “AllowNonAdminUserApprovals.” This new option on the Kernel Extension profile payload will allow standard users to approve a restart that rebuilds the Kernel Cache for Kernel Extensions approved by MDM. Kandji will support this new Kernel Extension profile payload option in a future update.
Additionally, on future Apple Silicon based Mac computers, in order for an MDM solution to approve Kernel Extensions as well as install Software Updates, the device will need to have a Bootstrap Token escrowed to MDM (see previous section on changes to Bootstrap Tokens), and be enrolled into MDM via Automated Device Enrollment. Devices enrolled manually will have to enable this ability for MDM inside of macOS Recovery.
Transition to Apple Silicon
Apple announced that they’re transitioning the Mac to Apple Silicon, a broad term they coined to refer to their custom chips and other technologies. While most existing apps built for the Intel-based Mac will continue to run with Rosetta 2 emulation technology, Developers can begin updating their apps now to take advantage of the performance boost that Apple Silicon will provide.
In the press release, Apple stated that macOS Big Sur is packed with new features that will make the transition to Apple Silicon seamless. One of these features is the ability for developers to build Universal 2 application binaries that include support for both Intel and Apple Silicon. This has important implications for Mac admins.
Another exciting feature gives developers the ability to make their iOS and iPadOS apps available on macOS – without making any modifications. Apple will begin the transition near the end of 2020, and they expect it will be complete in about two years. Regardless, developers can prepare now, and IT can try to get ahead of the inevitable testing and approval processes necessary before they can begin deploying silicon-based Mac computers. In a future version of macOS Big Sur, MDM solutions will be able to deploy iOS applications to Apple Silicon based Mac computers.
Read More About Apple Silicon:
You can read more about this in our Mac admins’ guide to Apple Silicon. In that guide, we also cover the particulars of why macOS will have the ability to run iOS apps, the new login experience, how macOS recovery is changing, the new Mac Sharing Mode feature, and more.
Automated Device Enrollment on macOS Big Sur
macOS Big Sur will continue to support the latest device management (MDM) features, like Automated Device Enrollment. Automated Device Enrollment saves IT time by automatically enrolling devices into an MDM solution. All users have to do is boot up their Mac, select a language, and connect to a Wi-Fi network.
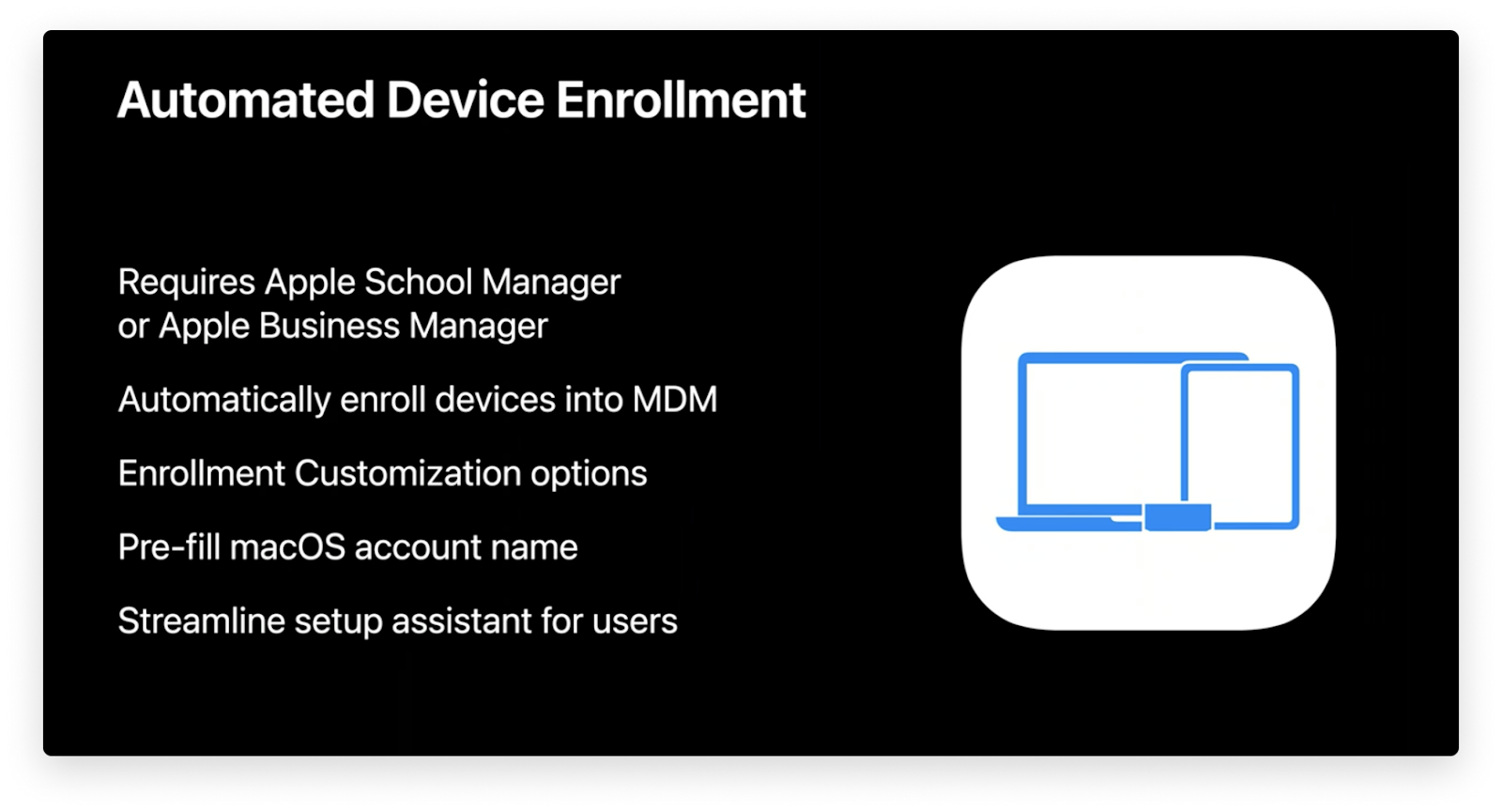 Image source: developer.apple.com
Image source: developer.apple.com
Using Enrollment Customization gives IT even more power over the enrollment process. This new feature lets IT add custom branding, consent text, and modern authentication to their teams during the setup period.
Because IT never has to interact with the devices physically, this is a great enrollment option for any business that needs to deploy a lot of devices. There’s also a great new feature to customize the enrollment process for your desired Setup Assistant workflow.
Read More About Automated Device Enrollment:
You can find more information about Automated Device Enrollment in our guide to Apple device enrollment methods, including ideal use cases, steps you need to take to set it up, and its compatibility with device supervision.
Lights Out Management Comes to Mac Pro
Apple announced a very powerful device management/Big Sur feature coming to the Mac Pro: Lights out Management (LOM). Lights Out Management lets IT remotely startup, shutdown, and reboot Mac Pro devices on their local network – even if the devices are unresponsive.
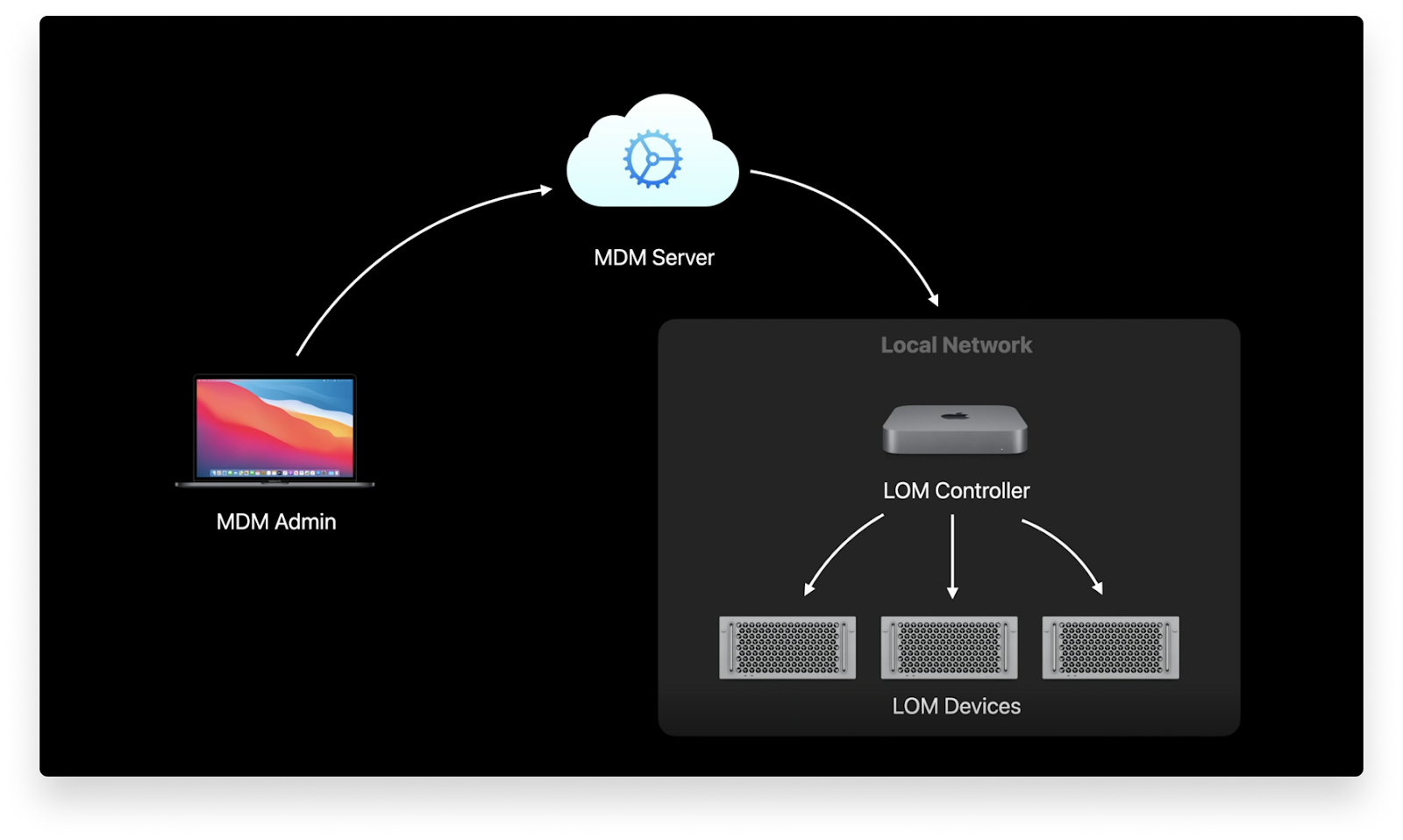 Image source: developer.apple.com
Image source: developer.apple.com
This requires using one Mac as a LOM controller for your local network (subnet over IPv6) and then enrolling your Mac Pro devices to that controller. Once they’re linked, IT can send commands to an MDM server, and then the LOM controller will distribute them to the enrolled Mac Pro devices.
Managed Apps on macOS Big Sur
Managed Apps were a powerful MDM capability on iOS, and now they’re coming to macOS Big Sur. Leveraging Managed Apps for macOS will let IT remove apps with MDM commands, have apps automatically removed upon device unenrollment, and even convert some unmanaged apps into Managed Apps.
Note: Managed App conversion isn’t supported for user-enrolled devices.
New Content Caching MDM Command for macOS Big Sur
Apple initially introduced content caching to speed up download rates and optimize the Internet usage of Mac apps, books, iCloud content, software updates, Xcode components, and more.
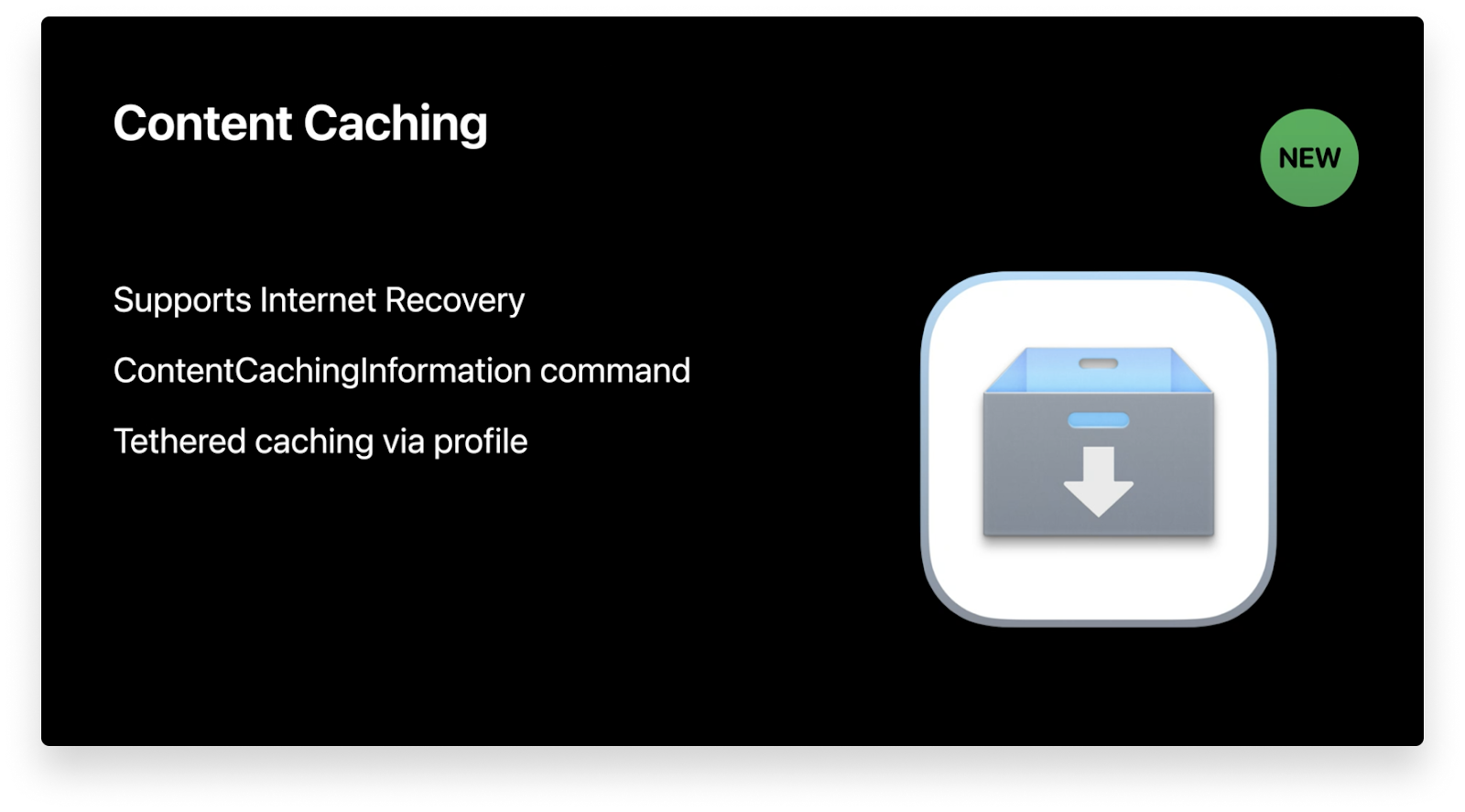 Image source: developer.apple.com
Image source: developer.apple.com
In macOS Big Sur, content caching has been expanded to support a wider range of data types and to include an Internet recovery feature. Apple also announced a new MDM command, ContentCachingInformation, that IT can use to see important caching metrics.
Security Updates for macOS Big Sur
Apple also announced a few other security updates for macOS Big Sur. We’ll take a quick look at them here:
- Prevent Accidental Profile Installation: Because profiles can configure devices, it’s important that they are only downloaded from trusted sites – and that users can’t accidentally install them. On macOS, users are now notified to review a profile that has been downloaded. In Settings, they can then choose to delete or install it.
- Prevent Silent Profile Installation: Similar to the previous security update, Apple added a new prevention measure to stop profiles from being silently installed via the profiles command-line interface. Now, any profile that’s downloaded via Command Line is treated as a downloaded profile, which will not take effect until the user chooses to install it in Settings.
- Limit Network Setup for Standard Users: The networksetup tool can be used to view and edit network settings using Terminal. Previously, standard users and IT administrators had the same capabilities using the tool. Now, admins retain full capabilities while standard users are limited to basic actions.
- Randomized Serial Numbers: Recognizing that device serial numbers can be used maliciously, Apple announced that their new devices will use randomized ten-character serial numbers.
There are a lot of device management changes coming to macOS Big Sur, and the entire Kandji team is excited to continue building out support for them in our MDM solution. With powerful features like zero-touch deployment, one-click compliance, and offline remediation, Kandji has everything you need to enroll, configure, and secure your devices.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.



