Introducing macOS Security and Compliance
 Kandji Team
Kandji Team
Editor's note: This post was originally published in 2019. For the latest updates on Apple MDM and related topics, check out our Recent News blog page. For more information on compliance in Kandji, check out our compliance product page.
Every company will at some point encounter the need to comply with a specific security or compliance framework, whether it’s to win a major customer, fulfill requirements to complete a round of funding or acquisition, or simply to prove that your company is secure, reliable, and worth doing business with.
That’s why we were surprised to learn that, for Mac devices in the workplace, there was no straightforward solution to meeting any of the major security standards or compliance mandates. Many of these mandates have device-specific controls, often called parameters, which govern everything from Bluetooth to screensaver settings. To ensure compliance, IT teams managing Apple devices need to be able to manage these parameters in one central place and provide proof to auditors that their devices are compliant.
The macOS Security and Compliance Landscape
These security and compliance frameworks exist because our rapidly evolving online ecosystem comes with new cybersecurity risks and because data privacy and governance is important. To instill trust, companies need a system of benchmarks to prove they are following best practices. If you are buying software, you want to know that any of your data housed in that system will be kept secure, and you need a standardized framework to prove it.
Here are some common security and compliance frameworks:
- CIS Benchmark for macOS: The Center for Internet Security (CIS) outlines a gold standard for how companies globally should approach IT security and compliance. CIS has published 100+ configuration guidelines for various technology groups. CIS has worked with the Apple community since 2009 to publish a benchmark for each version of Apple’s macOS. The CIS benchmark for macOS includes recommended settings such as disabling screen sharing, turning off Bluetooth if no paired devices exist, or disabling guest account logins. Kandji is a CIS partner and our software has been awarded the CIS Security Software Certification for CIS Benchmarks.
- FedRAMP Compliance for macOS: The Federal Risk and Authorization Management Program (FedRAMP) helps provide a standardized approach to security for cloud-based services. If your company plans to sell to, service, or work with a government agency at any point, you will likely need to maintain FedRAMP compliance. Included within FedRAMP’s robust framework is a requirement to meet the latest CIS benchmark for macOS, so some consider FedRAMP as an extension of CIS.
- NIST Compliance for macOS: The National Institute of Standards and Technology (NIST) is part of the US Department of Commerce, and is best known for its cybersecurity frameworks, which help protect organizations against cyber threats through best practices such as running penetration tests, studying threat intelligence feeds, employing Security Information and Event Management (SIEM) solutions, and more.
- DISA STIG: Commissioned by the US Department of Defense, the Defense Information Systems Agency (DISA) offers another layer of security based on configuration standards called Security Technical Implementation Guides (STIGs), which provides guidance on how to lock down information systems/software that might otherwise be vulnerable to a malicious computer attack.
The biggest challenge with these frameworks is that most IT teams don’t know where to start, and your mobile device management (MDM) solution may only cover a handful of the needed controls for each framework.
If your MDM solution does not include a control that you need, you generally have to create a custom script to perform a command or manage specific system configurations, and then run a remediation script to resolve any errors and confirm the command was completed successfully. This requires many hours of skilled labor and makes it complicated to maintain your scripts over time, adjust your settings in the future, or prove compliance to auditors. We knew there had to be a better way — so we built Kandji.
Introducing macOS Security and Compliance
Before we were Kandji, we ran an Apple-certified IT firm that served modern businesses running on Apple. We were the people painstakingly rolling out macOS compliance mandates to thousands of Apple devices for some of the biggest names in tech. We’ve felt gaps in the MDM market because we spent over a decade deploying every MDM on the market.
In this post, we’re excited to highlight something we’ve been working on for a long time: macOS security and compliance, built right into Kandji’s Apple MDM solution.
150+ Pre-Built Parameters
When we built Kandji, we wanted to take all the knowledge gained from working on these complex compliance projects and create the first one-click parameter library on the market. Instead of putting the burden on IT to custom-build controls to meet these standardized compliance frameworks, we wanted our customers to be able to enable each one with just one click. Kandji is the only MDM with this kind of pre-built library of security controls to automatically enforce compliance mandates. At the time of this writing, our library has over 150 one-click parameters, although we know this number will continue to grow.
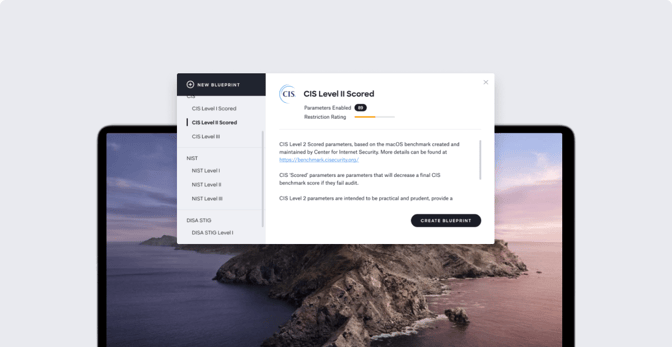
One-Click Compliance Templates
In addition to the individual parameters, we also wanted to create groups or sets of parameters that were associated with a specific level of security or compliance framework. Kandji offers two types of templates:
- Security Best Practices (Kandji Level I-IV): These are Kandji-built templates that embody industry best practices based on different levels of sophistication. For example, for smaller customers in less regulated industries, we recommend starting with Kandji Level I and then layering on additional controls as needed. Enterprise customers in highly regulated industries may require Kandji Level IV.
- Standardized Compliance Frameworks: We have also grouped parameters based on the compliance mandates they are associated with. For example, you may apply a template for CIS Level 1 Scored or CIS Level 2 Scored, providing you with a starting point for following CIS best practices according to your needs.
Offline Remediation
As mentioned above, another point of friction we wanted to solve for with Kandji was the level of detail and manual work involved in building and maintaining remediation scripts.
Say, for example, you assign a control to a device instructing it to lock the screen after two minutes. First, you need a way to confirm that your control has been completed successfully. Then, if it failed, you need a way to fix, or remediate, the issue and confirm the fix was successful.
The problem we encountered was that other MDM solutions did not include the remediation step out of the box. That meant we had to create custom remediation scripts for hundreds of controls per client, and then maintain those scripts over time. Managing remediation manually is painstaking to maintain, much less scale.
There was also another problem – other MDM solutions were not able to do anything if a device was offline. That meant we had no way to enforce compliance while a device was offline.
When we built Kandji, we made sure remediation was baked in from the very beginning. Kandji is the only MDM that works around the clock to enforce compliance and remediate issues, whether your Mac devices are online or off. This functionality is made possible by our macOS agent, which extends your capabilities beyond the expected to ensure you are always in compliance.
Auditor Access
Once all the work has been done to achieve a certain compliance framework, the final step is to prove to security and compliance auditors that you should be awarded a certain security or compliance status.
We make this easy in Kandji by providing an auditor-specific access level. The easiest way to prove macOS compliance with Kandji is to add your auditor(s) using this auditor access level, which provides them with read-only access. The only exception is that auditors have the option to enroll a device, in case they need to test any functionality (although this can be disabled if needed). Since Kandji provides an unprecedented level of visibility (detailed records, key updates, and an extensive log of remediations performed on each machine), auditors will have everything they need to prove that your company is in compliance.
As the only MDM with a pre-built library of security controls (over 150 and growing), Kandji includes the industry’s first macOS compliance framework that automatically enforces and remediates issues, even when your devices are offline. With Kandji, you can be confident that your Apple fleet is in safe and secure hands from deployment to retirement.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.