Extensible Enterprise SSO Framework: Kerberos Extension and What’s New with Big Sur
 Kandji Team
Kandji Team
Apple’s Extensible Enterprise SSO (single sign-on) framework has big implications for device management and authentication. In this article, we’re going to take a look at how the Kerberos single sign-on extension works, what it can do for you, and how you can configure and deploy it. We’ll also discuss how Kandji’s SSO Extension Profile makes it easy to leverage the Kerberos Extension.
Here's an overview of this guide:
- A Primer on SSO Extensions
- What’s the Kerberos Single Sign-On Extension?
- Building and Deploying a Kerberos Configuration Profile
- What’s New in macOS Big Sur Kerberos Extensions?
A Primer on SSO Extensions
At the World Wide Developers Conference (WWDC) 2019, Apple introduced the Extensible Enterprise Single Sign-On (SSO) framework. SSO lets users access multiple applications with a single set of credentials, simplifying the authentication process and streamlining the login experience for both native and Safari-based applications.
What makes this possible are redirect and credential SSO extensions, which let identity providers (IdPs) build programs that can achieve seamless SSO experiences. One such program is the Microsoft Enterprise SSO plug-in for Apple devices, which we’ll talk about later in this article.
Using these extensions requires a device management (MDM) solution – to enable them, you need to deploy the extensible SSO MDM profile (and associated domains for redirect credentials). We’ll get into more depth on what these extensions are and how they’re deployed next.
What are Redirect Extensions?
Redirect extensions are intended for modern authentication methods, such as OpenID Connect, OAuth, and SAML2. You can use them for authentication with Safari and native applications.
Deploying redirect extensions requires an MDM payload and associated domains. The payload must be delivered using your business’ MDM solution. For the information regarding the payload’s redirect configuration, you can read our Identity and SSO guide.
As for associated domains, these simply ensure that you own the traffic that’s being redirected. You need to configure associated domains in the host app that contains your extensions, which you can read about in Apple’s support documentation.
What are Credential Extensions?
Credential extensions are intended for challenge/response authentication. These extensions request data and then get challenged for authentication, unlike redirect extensions, which request credentials before data. They can also be used for Safari and native apps.
If you want to deploy a credential extension, you don’t need to worry about associated domains, which were necessary for redirect deployment. You just need to deliver a credential payload using your business’ MDM solution. You can find information on this payload in the guide we mentioned earlier.
What’s the Kerberos SSO Extension?
The Kerberos Single Sign-on extension is a credential extension designed to manage Kerberos/Active Directory credentials, synchronize local and Directory passwords, and support authentication via smart cards, MDM-provided certificate-based identity, and username/password. Included in iOS 13, iPadOS, and macOS Catalina, this extension is a replacement for Enterprise Connect.
Though Kandji fully supports Apple’s Extensible Enterprise SSO framework, most IdPs are still in the process of developing support for it. If you’re curious if your IdP is working on this extension or are uncertain when it will be ready, we recommend encouraging them so you can leverage the Extensible Enterprise SSO framework (for macOS and iOS) as soon as possible.
Microsoft released a public preview, available for iOS, called Microsoft Enterprise SSO plug-in for Apple devices. This plug-in can achieve SSO for Azure AD accounts across any compatible iOS apps that leverage Microsoft Authentication Library (MSAL). For information about enabling this SSO extension with your MDM solution or using it in an application, you can read Microsoft's documentation.
Why is Microsoft the only one that’s ready? We can only speculate, but so far they’ve developed the most comprehensive solution. While we haven’t heard anything official from Microsoft, we can speculate that the macOS version of the Extensible Enterprise SSO Extension may be ready by the end of 2020.
Transitioning from Enterprise Connect
The Kerberos Single Sign-on extension replaced a similar tool called Enterprise Connect. Transitioning to Kerberos isn’t necessary if you’re upgrading your Mac computers to macOS 10.15 (Enterprise Connect will still function as usual). Still, Apple advises businesses to begin making plans to transition to Kerberos.
In the support documentation on the Kerberos Single Sign-on extension, Apple says Kerberos will meet the needs of the vast majority of organizations. However, if your business meets the following criteria, you may not be able to transition from Enterprise Connect, or you may only be able to achieve a partial transition:
- If you use an MDM solution that doesn’t support user-approved MDM (UAMDM) enrollment, or if you aren’t using an MDM solution at all.
- If you have Mac computers running on macOS 10.14 or earlier. In this case, Apple advises that you leave these systems on Enterprise Connect until you upgrade them to macOS 10.15.
- If you’re using an Active Directory functional level of Windows Server 2003 or earlier.
Functions of the Kerberos Single Sign-On Extension
Before we break down how you can build and deploy a configuration profile for this extension, we’re going to do a quick survey of the functions that Kerberos authentication (for macOS and iOS) can perform. For complete details of what the Kerberos Single Sign-on extension can do, you can read the support documentation that we mentioned earlier.
Live password testing: You can use the Kerberos extension to test user passwords in most configurations of Active Directory. This includes informing users of password requirements while creating a new password, as you can see in the image below.
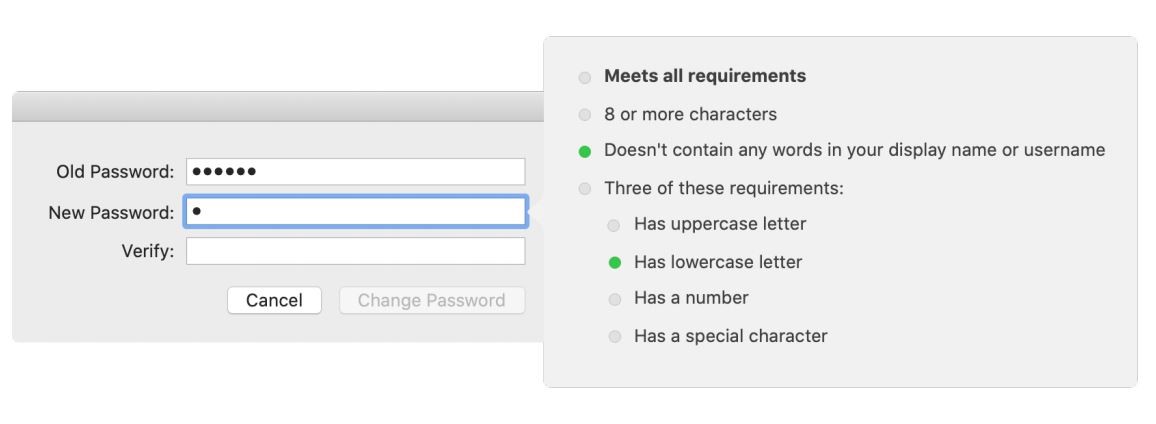
Password requirements display: If you can’t use the live password testing function, you can configure the Kerberos Single Sign-on extension to display your business’ password requirements as users enter their new passwords. This requires setting “pwReqText” in your configuration profile to a string containing the text you want to appear.
Changing or disabling password functionality: If you don’t allow password changes against Active Directory, then you might not be able to use the standard password change functions of the Kerberos Single Sign-on extension. To disable this function, set “allowPasswordChanges” to FALSE in the configuration profile.
Password change website support – (Mac): You can configure the Kerberos Single Sign-on extension to open a password change website when users select “Change Password” or interact with a password expiration notice. Apple only recommends using this feature for local accounts – mobile accounts aren’t supported. To do this, set “pwChangeURL” in your configuration profile to the URL of your password change page.
Password sync – (Mac): You can use the Kerberos Single Sign-on extension to sync users’ local account passwords with their Active Directory passwords. This requires setting “syncLocalPassword” to TRUE in the configuration profile.
Smart card support -(Mac): You can also use smart card-based identities for Kerberos authentication (Mac only). However, token-based drivers are not supported, so the smart cards must have a CryptoTokenKit driver available. To use this function, you must make sure that your Active Directory domain is configured to support smart card authentication.
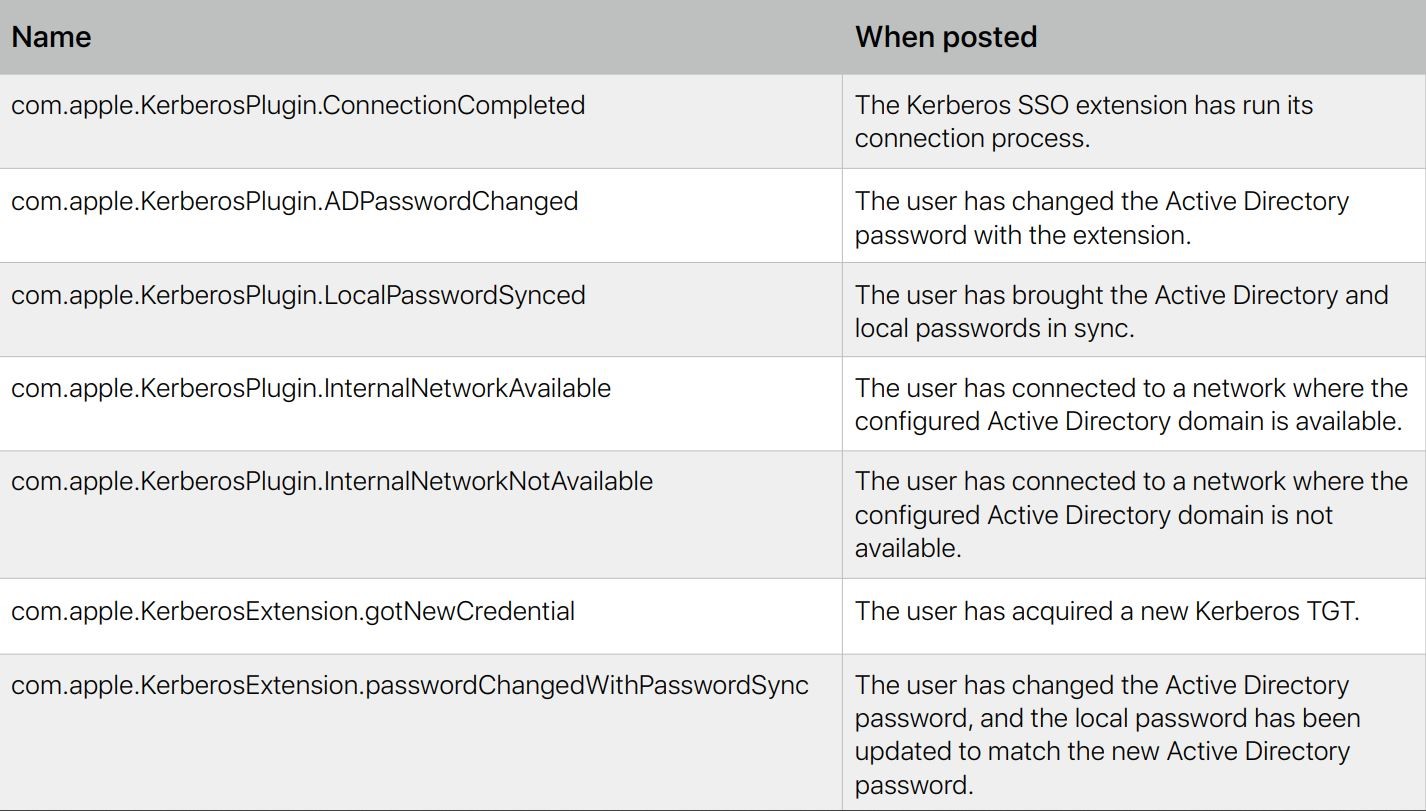
Distributed notifications - (Mac): When an event occurs, macOS apps and services can use distributed notifications to communicate relevant information with other apps and services. You can use the Kerberos extension to post the following distributed notifications:
Kerberos Extension Command-line support (Mac): If you want to access helpful information and have more control over the Kerberos Single Sign-on extension, you can use a command-line tool called app-sso. This tool can perform functions such as initiating a sign-in, password change, and sign-out. You can also use app-sso to print information, which can be uploaded to your MDM solution.
Mobile Accounts (Mac): As we covered earlier, Apple recommends using the Kerberos Single Sign-on extension with a local account. However, if you still choose to use mobile accounts with the Kerberos extension, you must be aware that, according to Apple's Kerberos guide:
If you use the Kerberos SSO extension to change your Active Directory password and you’re logged in to your Mac with the same user account you’re using with the Kerberos SSO extension, password changes function as they do from the Users & Groups preference pane. But if you perform an external password change—meaning you change your password on a website, or your help desk resets it—the Kerberos SSO extension can’t bring your mobile account password back in sync with your Active Directory password. Using a password change URL with the Kerberos extension and a mobile account is unsupported.
Quote source: apple.com/business
Domain-realm mapping: While Apple’s operating systems can almost always determine domain-realm mapping, you may need to define a custom domain-realm map if your Kerberos realm authenticates with a resource using a different domain. You can define your domain-realm map in the configuration profile.
Building and Deploying a Kerberos Configuration Profile
Using the Kerberos Single Sign-on extension requires building a configuration profile and delivering the profile to your devices using an MDM solution. On macOS, manually adding the profile isn’t supported – it requires user-approved MDM enrollment and installation in the System scope. In this section, we’ll walk you through the process of building the configuration profile and completing the user setup process.
How to Build a Kerberos SSO Extension Configuration Profile:
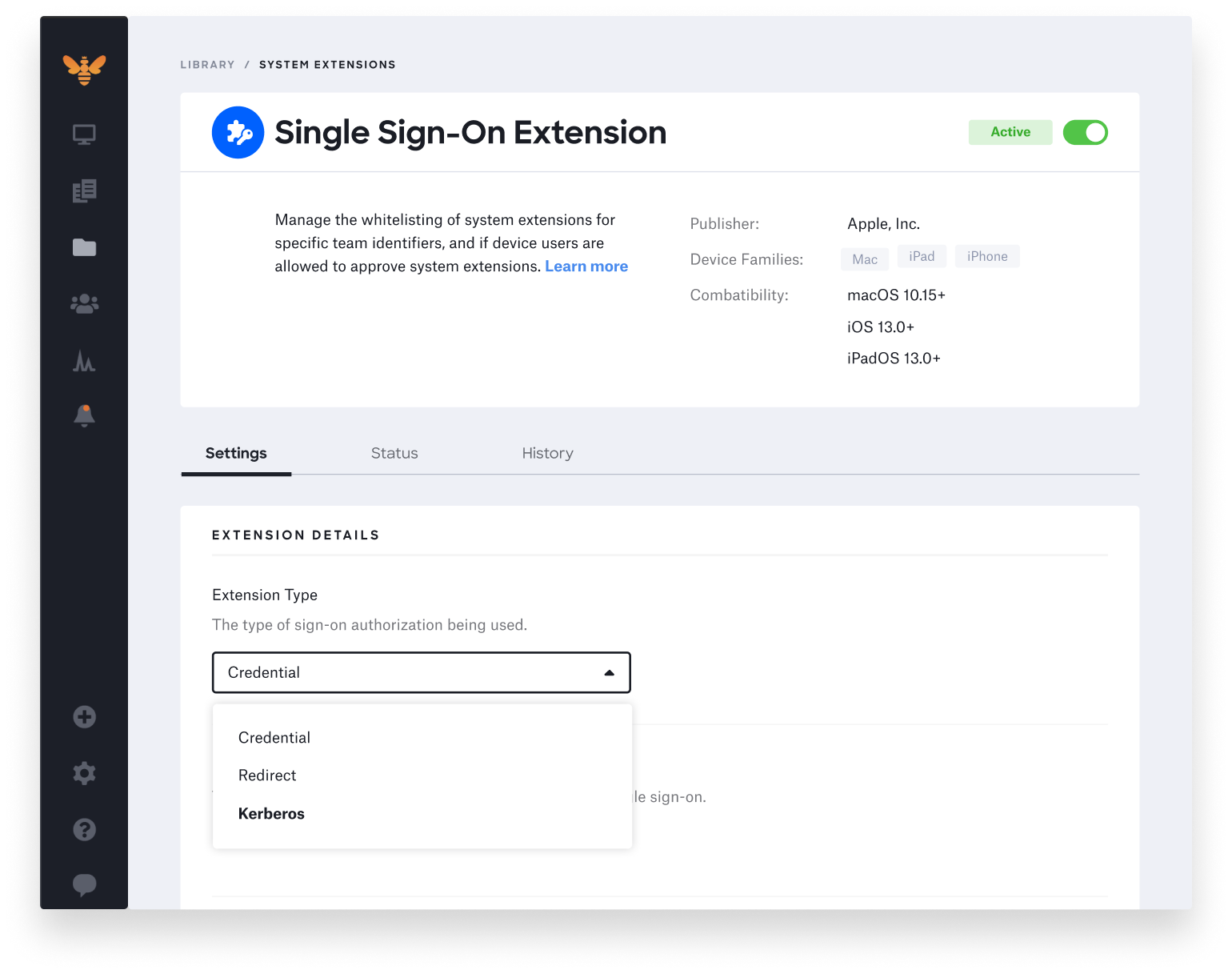
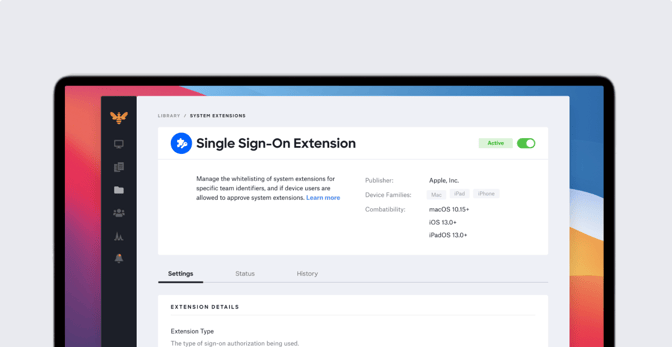
Here at Kandji, we built a new SSO Extension Profile with built-in support for the Kerberos single sign-on extension. Using Kandji’s SSO Extension Profile takes the manual work out of creating a Kerberos extension.
Kandji’s SSO Extension Profile also includes an easy-to-use interface, so you don’t have to create and upload a plist file to fill in all the Kerberos keys and options. Kandji supports all the Kerberos options we discussed earlier in this post. Here’s a sample of what it looks like:
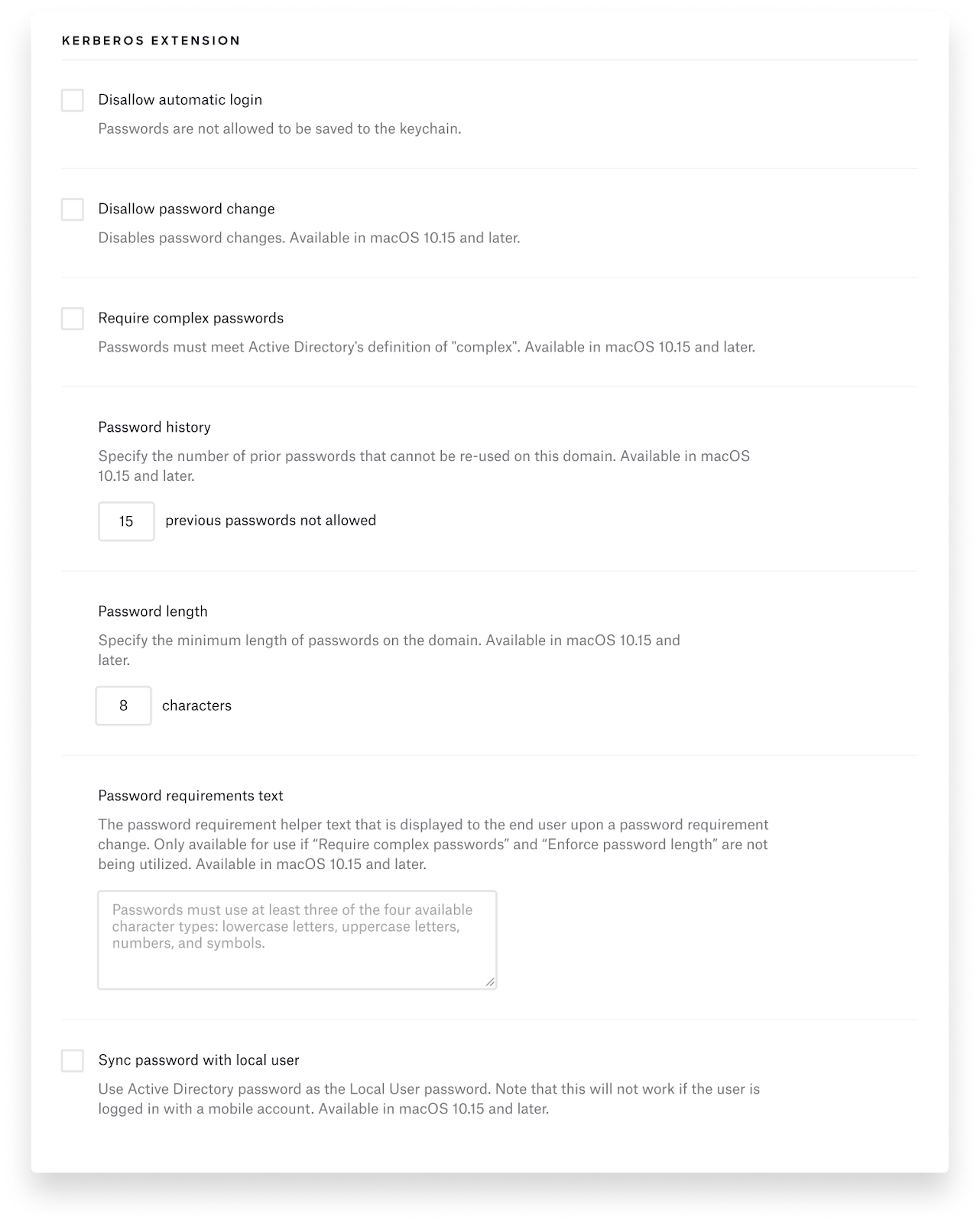
This makes it easy for IT administrators to use Apple’s new Extensible Enterprise SSO capabilities. To learn how to take advantage of this new profile, read our SSO Extension Profile support article.
iOS and iPadOS User Setup
- Connect Your Device: Connect your device to a network where your organization’s Active Directory domain is available.
- Access a Platform that Supports Kerberos Authentication: Open a Safari website that supports Kerberos authentication, or launch an app that supports Kerberos authentication.
- Sign in to the Platform: Enter your Kerberos or Active Directory login credentials to sign in to the platform. Answer the prompt asking if you want to sign in automatically. Next, select Sign In.
After a moment, your website or app will load. If you chose to automatically log in to the Kerberos Single Sign-on extension, you won’t have to enter your credentials until you change your password. If you didn’t choose to sign in automatically, you will need to log in again once your Kerberos credential expires. This usually takes 10 hours.
macOS User Setup
1. Authenticate to the Kerberos SSO extension: You can access a platform that supports Kerberos authentication for macOS in several ways:
- If your Mac is connected to the network where your Active Directory domain is available, you’ll be prompted to authenticate after the Extensible SSO configuration profile is installed.
- If you’re using a Safari website or app that accepts Kerberos authentication for macOS, you’ll be prompted to authenticate.
- If you connect your Mac to a network where your Active Directory is available, you’ll be prompted to authenticate.
- If you select the Kerberos SSO extension menu extra, you can click Sign In to authenticate.
2. Enter Login Credentials: Once the authentication prompt appears, you’ll need to enter your Active Directory username and password. Once this is completed, answer the prompt asking if you want to sign in automatically. Next, select Sign In.
Just like the iOS and iPadOS setup process, if you chose to log in to the Kerberos Single Sign-on extension automatically, you won’t have to enter your credentials until you change your password. If you didn’t choose to sign in automatically, you will need to log in again once your Kerberos credential expires. This usually takes 10 hours.
On macOS, you’ll receive a notification if your password is close to expiring. To change your password, simply click on this notification and begin the password change process. If you enabled the password sync function that we discussed earlier, you may need to enter your Active Directory and local passwords, then click OK to sync your passwords.
What’s New With the macOS Big Sur Kerberos Extension?
At WWDC 2020, Apple announced some exciting updates for the macOS Big Sur Kerberos Extension. In this section, we’re going to take a look at what’s new:
Menu-extra Updates: The menu-extra for macOS is now more representative of the state of the extension. It will show a “solid” key icon if all of the extension requirements are met. These requirements include having a credential, active network connection, functioning DNS, and an unexpired Kerberos ticket. If these requirements are unfulfilled, it will indicate what’s missing and show a “faded” key icon.
Customizable UI: Because all organizations don’t use the same name for their identities, Apple has included the ability to customize the label that’s shown in the Kerberos extension so it can match the name of your identity and organization. Apple also added the capability to add help text to guide users through login issues. This text is displayed beneath the login panel, so it can include contact information for your IT help desk so users can easily get the support they need.
Better Support for Per-App VPN: The Kerberos Single Sign-on extension will now trigger Per-App VPN for authentication-only requests. This lets you log in without manually triggering the VPN or having a separate network request. On macOS, the extension also supports app-to-per-app VPN.
User-Channel Support for Certificate-Based Kerberos or PKINIT: Referencing user-level certificate identities in a system-level scoped profile has always been available while configuring the Kerberos extension. However, with Apple’s latest improvement will make it much easier for MDM vendors to bundle configurations and certificates together.
More Control Over First Login Experience: This new feature will delay the first login prompt until the first authentication challenge is received or until an administrator enables it.
The entire Kandji team is dedicated to making the most out of the evolving SSO landscape. With our new SSO Extension Profile, you can spend less time configuring and more time leveraging Apple’s new capabilities. This is just one part of a suite of features, such as zero-touch deployment, one-click compliance, and offline remediation. Our MDM solution makes it easy to enroll, configure, and secure your devices. 
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.