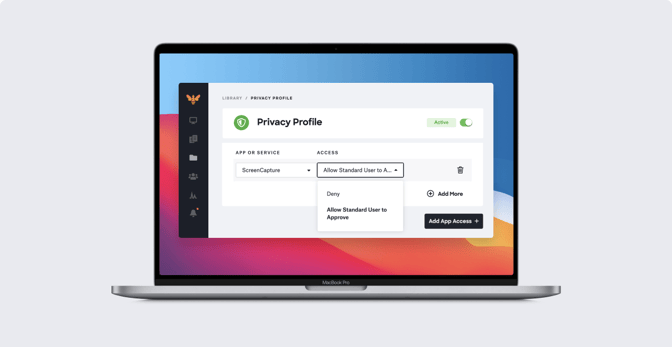
Apple recently announced new changes coming to PPPC on macOS Big Sur. With macOS Big Sur, standard users are prevented from approving applications for certain sensitive system-level PPPC controls, Screen Recording and Input Monitoring, which was not the case for macOS Catalina.
However, a more recent release allows IT to use MDM and the PPPC profile to allow standard macOS users to approve defined applications for Screen Capture and Input Monitoring on macOS Big Sur.
In this quick article, we’re going to see what’s changing and explore what its implications are for Mac device management.
A Primer on PPPC
In macOS Mojave, Apple introduced a set of security controls referred to as Privacy Preferences Policy Control (PPPC). These tools gave IT more control over cross-application data requests, such as if certain apps could access protected user and system resources without prompting users for approval. These resources include access to Desktop, Documents, Contacts, and other sensitive features like screen capture, camera, microphone and input monitoring.
In macOS Catalina, the ability for standard users to approve apps to access some of these system-level sensitive features was enabled by default. These features included screen capture and input monitoring. For MDM, these PPPC features were considered “deny only.” So, IT had no power to enable them via MDM and had to rely on users to provide approval.
While standard users on macOS Catalina were able to approve apps on their own to access these features, in an early beta of macOS Big Sur, this was initially changed to require admin authentication. This made it impossible for standard users to approve screen capture and input monitoring for common business apps, like Zoom, without admin approval.
The latest updates to PPPC in macOS Big Sur changes this.
What’s Changing in PPPC?
Previously in macOS Catalina, any local user (standard or admin) could approve screen capture and input monitoring PPPC requests. This has changed in macOS Big Sur. Now, IT can use MDM to pre-allow certain apps to be approved even by standard users to enable screen capture or input monitoring.
Before this change, MDM solutions could only specify a “deny only” status to prevent specific applications from requesting these PPPC features. In macOS Big Sur, MDM can replace the previous Allowed boolean key with a new Authorization key. You can see this in the image below:
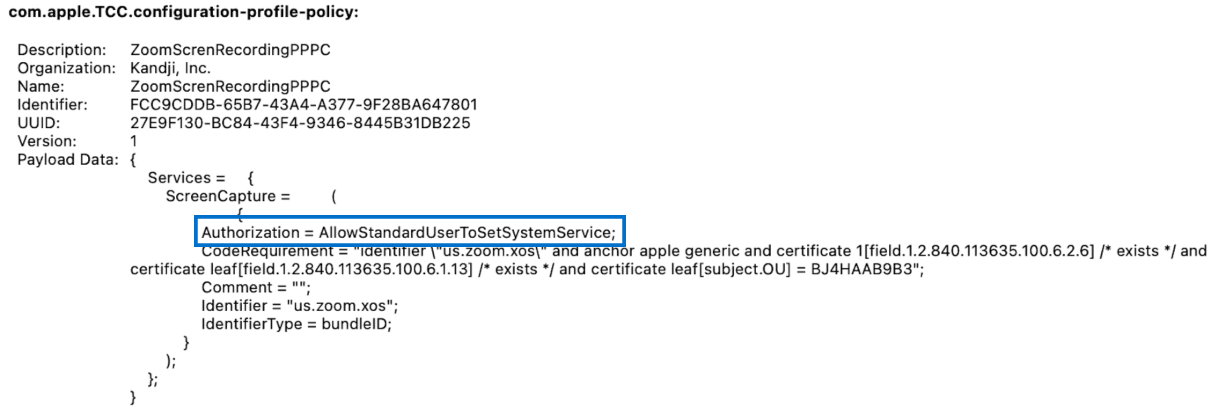
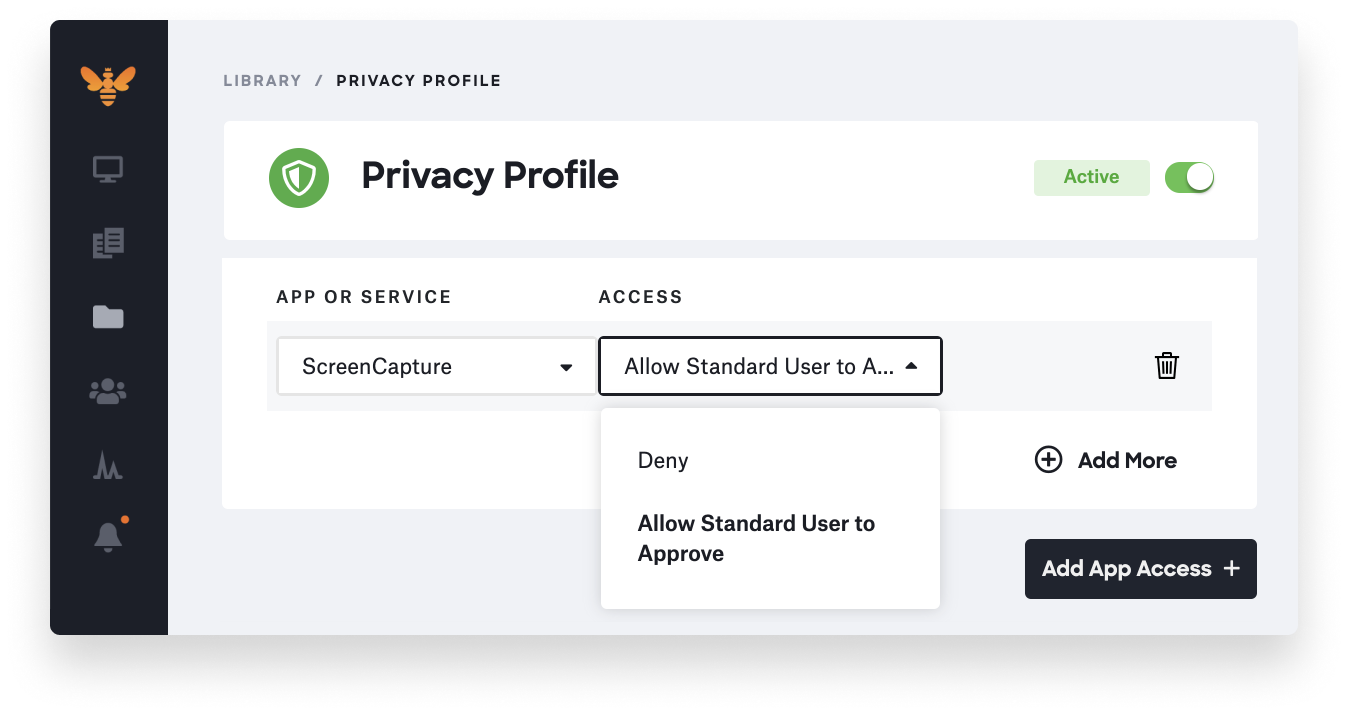
Now, IT can set this new Authorization key to a string value of “AllowStandardUserToSetSystemService.” This gives IT the ability to pre-allow some apps to let standard users approve or deny screen capture and input monitoring PPPC requests.
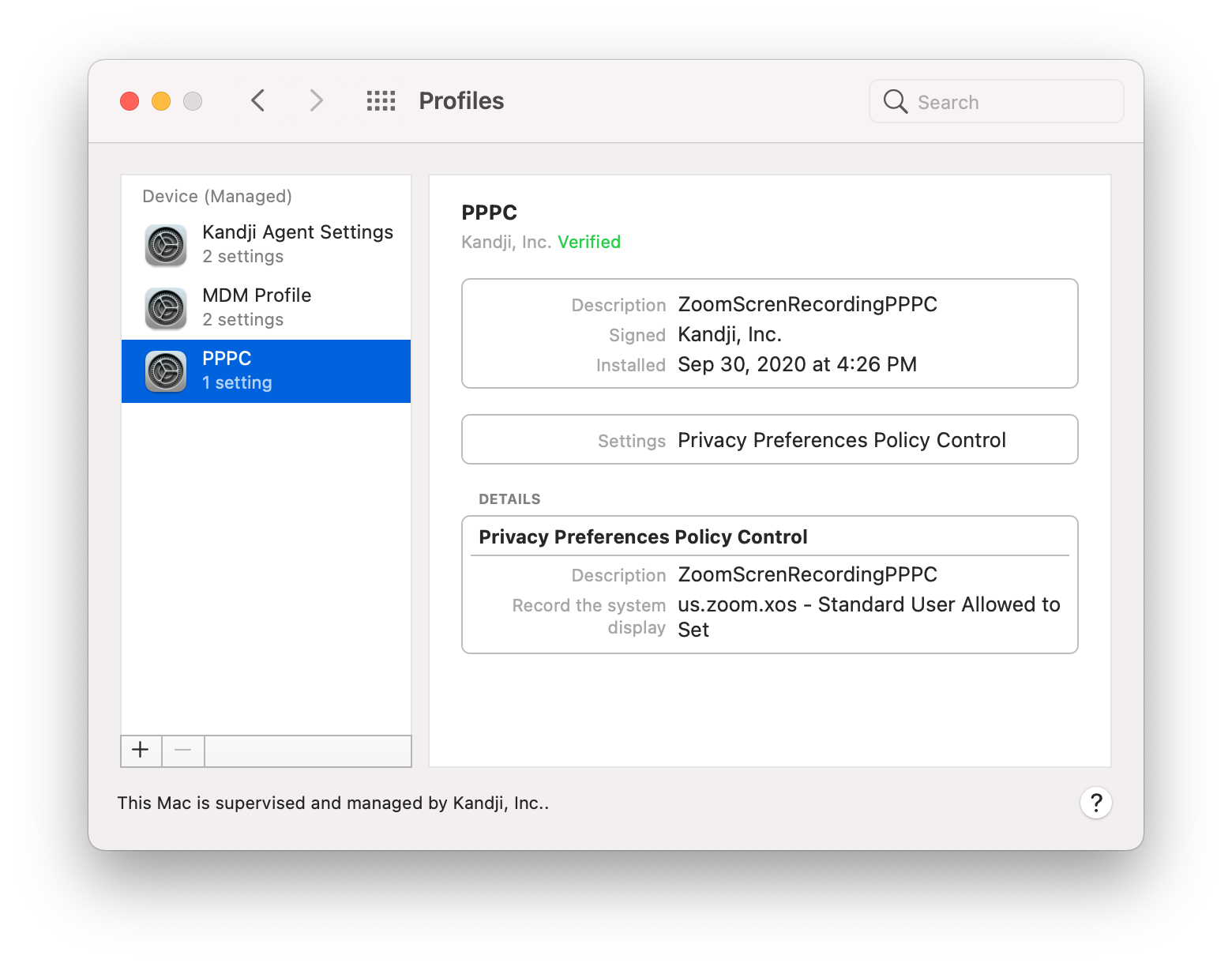
This will put the power in users’ hands to make their own decisions about which apps can participate in screen capture and input monitoring. However, standard users can only approve these PPPC requests on apps that have been specified by MDM for standard user approval. For instance, you can see in the image below that this PPPC profile specifies that Zoom screen capture can be enabled by standard users:
Once MDM gives standard users permission to approve specific apps for screen capture and input monitoring, these apps will appear to users in System Preferences > Security & Privacy > Privacy. On this page, as you can see below, users simply need to check the box next to the apps that they want to approve. Standard users will only be able to enable the permission for applications allowed by MDM for standard user approval.
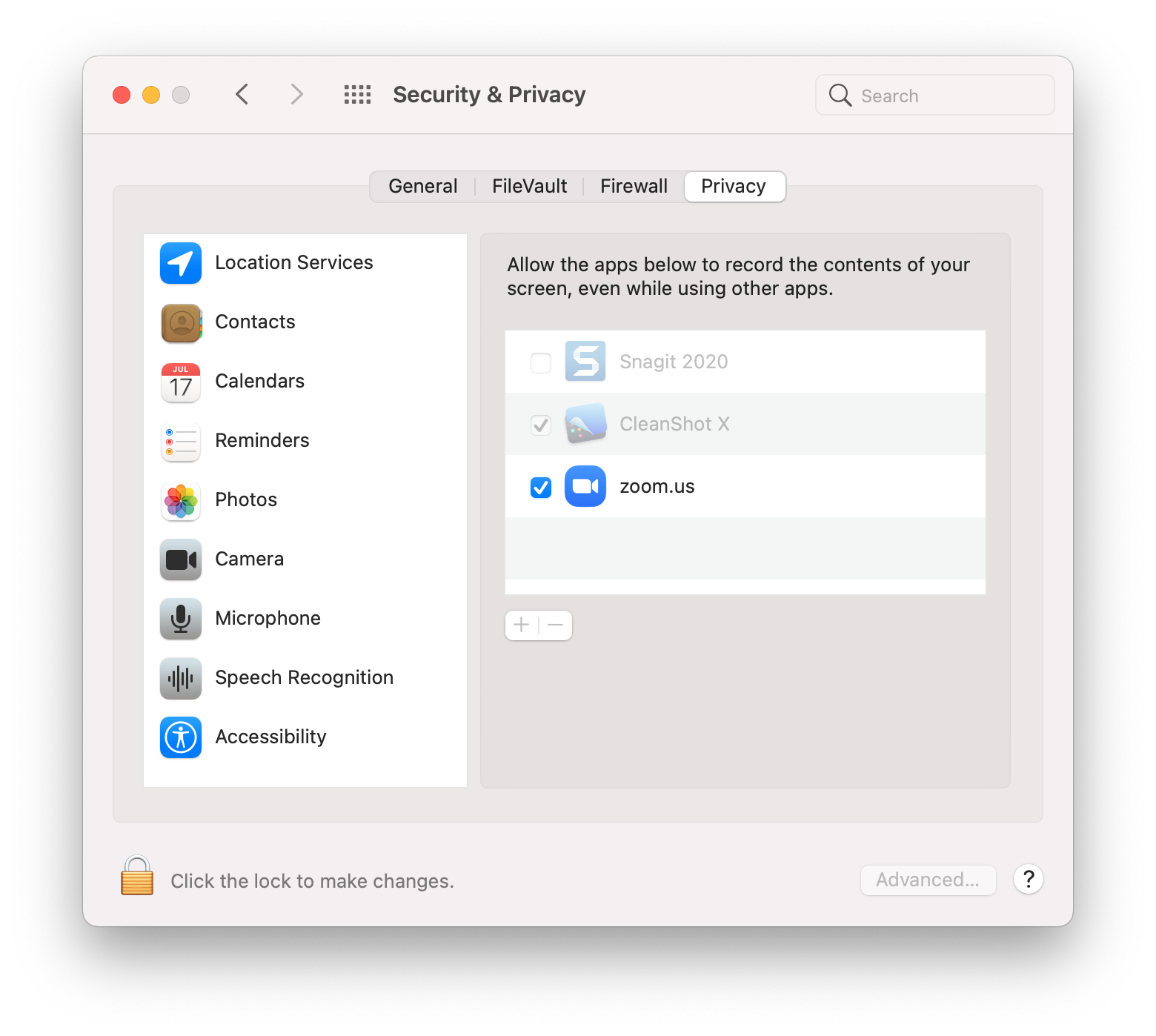
If the PPPC profile is removed, app permission will remain as long as it was granted beforehand, but standard users will no longer be able to make changes to it.
This update strikes a great balance between streamlining device management and trusting user consent for apps that access sensitive features. We’re excited to announce that Kandji supports these changes, which allows admins to use MDM and the PPPC profile to allow standard macOS users to approve defined applications for Screen Capture and Input Monitoring on macOS Big Sur.
With a suite of features such as pre-built security settings, zero-touch deployment, and one-click compliance, Kandji keeps your Apple devices safe and secure. 
 Kandji Team
Kandji Team