WWDC 2023: Changes Coming to Apple Device Enrollment
 Kandji Team
Kandji Team
Device enrollment—how you actually get a new (or not-so-new) device under management—is one of the standout features of Apple’s device management ecosystem. For new devices purchased through Apple itself or an authorized retailer, the process is practically seamless.
But there’s always room for improvement, and at this year’s WWDC, the company made a string of announcements aimed at making the enrollment process even smoother and more secure. It addressed some important edge cases and enabled more automation, all of which should make life easier for Apple admins across the board.
Automated Device Enrollment
The improvements start with a nice security update to Automated Device Enrollment. Admins will be able to move some important configurations earlier in the setup process and require a secure baseline configuration before the user can actually start using a device.
Previously, Setup Assistant would coast through to enrollment before doing most device configuration. That was nice for users, but it had a downside: Those users could start working with their devices before important security controls like FileVault were turned on, or the OS was completely updated.
With the updates that Apple announced at WWDC, it will be possible to enable FileVault and escrow a key right from Setup Assistant. That would ensure that every Mac is encrypted before there’s any chance that sensitive company data could be saved on it.
What’s more, Apple will allow admins to set a required OS version and, if that version isn’t installed yet, guide users through the update process before connecting the device to MDM. This would help ensure that compliance requirements are met right from the start.
Finally, Apple is also changing how macOS notifies users about enrollment if they set up the computer without network access. Under the new changes, when a user connects to a network, they can be presented with a full-screen Setup Assistant screen that will prompt them to either enroll in MDM or defer for 8 hours, when they’ll be required to complete enrollment.
Security teams, users, and IT admins can all celebrate these tweaks because they have the potential to allow for tighter security during device deployment without introducing new friction or drastically changing the setup experience.
Apple Configurator
When you’re enrolled in Apple Business Manager (or Apple School Manager) and buying devices from Apple or authorized resellers, enrollment happens more or less automatically: Devices enroll themselves on the first startup, and—depending on how your MDM vendor is set up—provisioning may not require any manual intervention at all.
But even then, there are edge cases, such as
- A recovered Mac that needs to be re-enrolled;
- An iPad that was donated;
- An iPhone you had to buy at the last minute—perhaps for a meeting or trade show—from a vendor you’ve never dealt with before.
For those times, there’s Apple Configurator. For most admins, it’s a fallback. But Configurator is nonetheless a surprisingly capable solution in its own right, and Apple has steadily improved its functionality over the years. This year the company announced some extremely welcome additions that make it even more powerful and easier to use than ever.
The first is a change in Apple Configurator for iPhone to the way devices are assigned to an MDM server after adding them to Apple Business Manager (or Apple School Manager). Previously, this was a two-step process: The device would first be added to an Apple Business Manager organization by scanning it with an iPhone. The administrator would then need to log in to the Apple Business Manager web portal and manually assign that device to their MDM server for management.
Now everything happens in a single step right in the app. Once a device is scanned into inventory, admins will be presented with a screen that allows them to assign it. They’re given the choice to not assign it to an MDM server (essentially the same behavior as before), assign it to a default server for that device type, or pick a specific server among those associated with the organization.
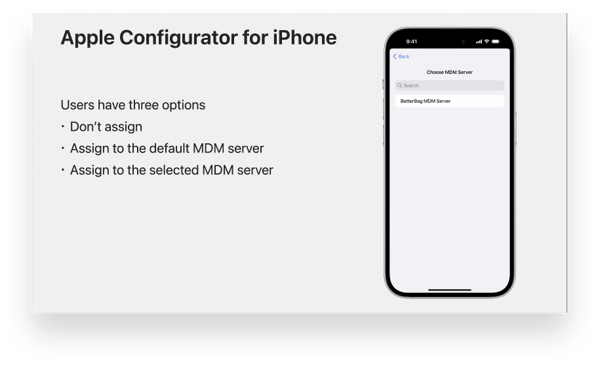
This might seem like a small change, but it does eliminate one of the few friction points in an otherwise smooth process. It makes Apple Configurator for iPhone a much more attractive choice for enterprise situations where multiple devices need to be enrolled at once.
There was also a major announcement at WWDC about Apple Configurator for Mac: adding Shortcuts actions. Similar to the Shortcuts apps that Apple has added to its operating systems over time, these new Configurator Shortcuts make it easy to string together a series of actions to do things like updating, restoring, erasing, and otherwise preparing iPhone and iPad devices for use.
With these Shortcuts, it will be possible for admins to build complete device enrollment and setup workflows that trigger automatically whenever a device is attached or detached to a Mac.
iPhone and iPad Return to Service
There’s one less reason to use Configurator at scale in the future, thanks to the announcement of something many admins have wanted for a very long time: a dedicated iPad/iPhone return-to-service workflow.
Until now, device redeployment has been bumpier than initial deployment, even for fully managed and supervised devices—especially those running iOS and iPadOS. That’s because the MDM Erase command fully wiped the device, including enrollment in an MDM solution and bindings to Apple Business Manager (or Apple School Manager). Redeploying that device thus required re-enrolling it manually or using Apple Configurator.
This has been fine for many use cases, in which a full wipe is an extraordinary step performed only at the end of life or when a device is lost or stolen. But there are also situations in which devices are wiped and redeployed as a matter of course: shared field service terminals, iPhones used in industrial applications, lab devices, and so on. For those cases, the additional manual work to return devices to service can keep IT teams very busy.
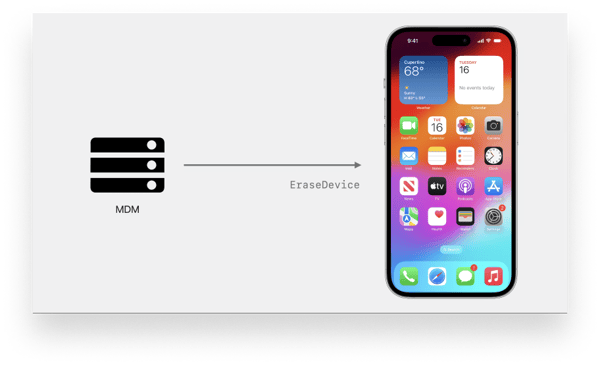
To help automate things, Apple is changing the way the MDM Erase command works for iOS and iPadOS. Admins can now deliver information with that command specifying the MDM server the device should enroll with and the WiFi configuration it should use. Together those bits of information mean a managed device that’s been erased can connect to the Internet and enroll itself the same way it did when it was first unboxed. If the device is already registered in Apple Business Manager (or Apple School Manager), it’s even easier—the MDM configuration can be omitted, and the device will re-enroll as normal once it is connected to a network.
This is great news for admins because it means the process of redeploying an old device is closer to the experience of deploying a new one with Automated Device Enrollment. For companies that wipe devices frequently, it will be a huge time saver.
About Kandji
Kandji is the Apple device management and security platform that empowers secure and productive global work. With Kandji, Apple devices transform themselves into enterprise-ready endpoints with all the right apps, settings, and security systems in place. Through advanced automation and thoughtful experiences, we’re bringing much-needed harmony to the ways IT, InfoSec, and Apple device users work today and tomorrow.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.
See Kandji in Action
Experience Apple device management and security that actually gives you back your time.



